Overview
Sococo is protecting customer's information in several different ways. All the communication between clients and servers is encrypted, all the installation files are signed, and data on servers is secured.
Note: if you suspect there has been a security breach by a member of your organization, please notify the support team to investigate the incident.
Information
No matter if you are using Sococo with browser or desktop app, your connection is always secure and your data is protected.
Sococo web app
Google Chrome browser
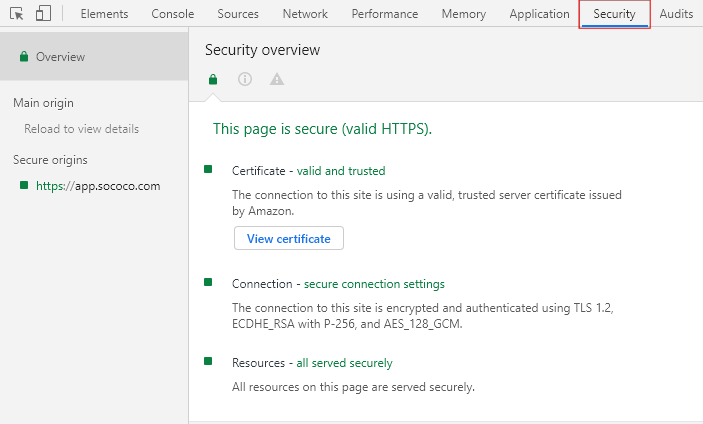
Sococo web application is presented over HTTPS, using AES_128_GCM (128-bit) encryption between clients (browsers and desktop app) and Sococo servers.
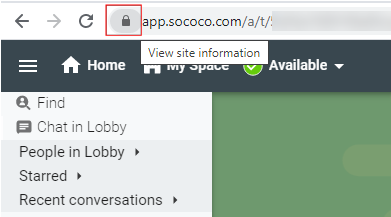
To review the certificate on your browser, you can check the lock icon next to your Sococo URL.
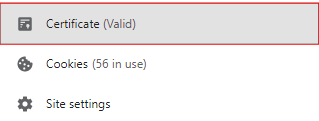
In the menu, you can see if the Certificate is Valid or Invalid. To review details, click on Certificate.
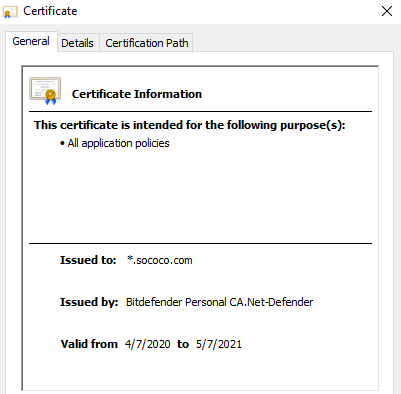
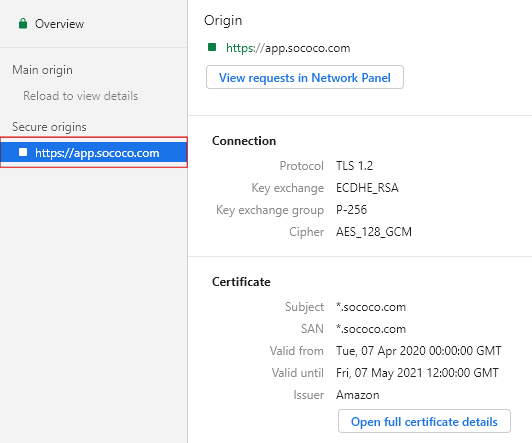
In the General Section, you can review who issued the certificate, and date until it is valid.
Sococo Desktop app
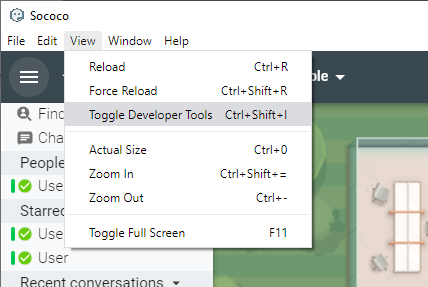
Using the Sococo Desktop app, you can review the Network Security by going to the View > Toggle Developer Tools.
Select Security in the DevTools, and see information in Overview.
For certificate details, you can click on the recorded activity for app.sococo.com under the Secure origins.
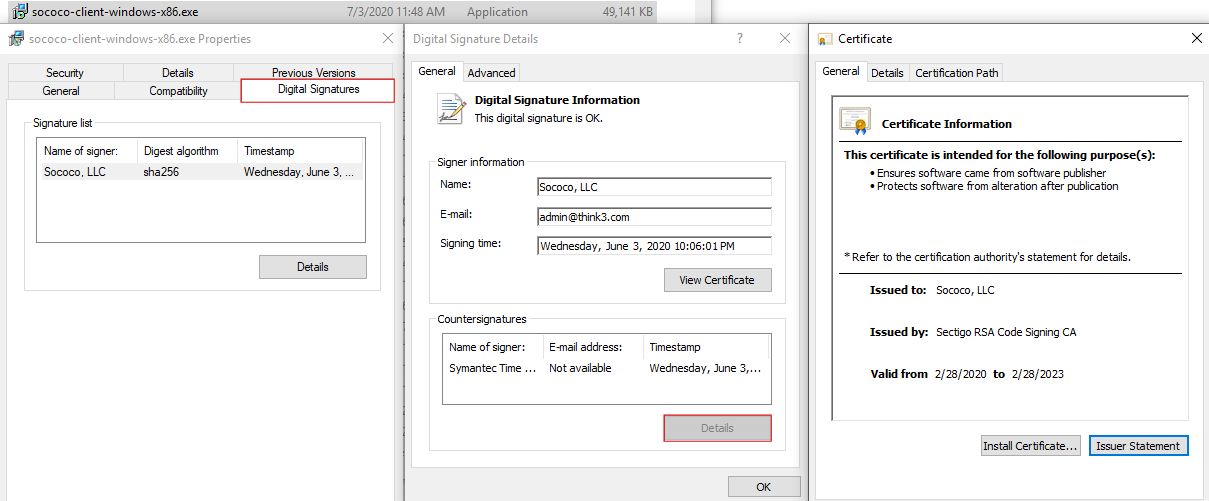
Additionally, Sococo desktop application installer is signed with Digital Signature by Sococo, LLC, so that you know you are installing the correct application.
Server-side
Sococo clients are establishing connections to Sococo servers hosted by Amazon Web Services (AWS). Both Sococo and AWS take Data Protection very seriously, using top-notch Security to protect your information.
User Access Security
Sococo has allowed clients to decide how they want to manage their User Access Security. Administrators can configure passwords requirements by configuring minimal length, complexity and password reset time period.
Priyanka Bhotika
Comments